
这篇文章介绍一下一个用于使用容器化方式验证微软的Active Directory的方式,可以通过容器化的方式启动AD的服务,但是镜像到目前为止已经四年没有更新了,但经过验证,发现还可以用,在本地需要搭建测试环境的时候,可以考虑使用这个镜像凑合一下。
环境搭建 步骤1: 拉取镜像使用如下命令拉取镜像:
执行命令:docker pull dwimberger/ldap-ad-it
执行日志如下所示:
liumiaocn:ldap liumiao$ docker pull dwimberger/ldap-ad-it Using default tag: latest latest: Pulling from dwimberger/ldap-ad-it b7f33cc0b48e: Pull complete 43a564ae36a3: Pull complete efb75a810eee: Pull complete 2c0a2476726b: Pull complete 68f91b595c9d: Pull complete ef42f722f2d0: Pull complete 7a2aeb20edad: Pull complete Digest: sha256:0c636e55eb82e295a5da2e09c75e6c5067184fb70ea9f63e50c0e5dd7ab32080 Status: Downloaded newer image for dwimberger/ldap-ad-it:latest docker.io/dwimberger/ldap-ad-it:latest liumiaocn:ldap liumiao$ docker images |grep ldap-ad-it dwimberger/ldap-ad-it latest 63cf38b710f5 3 years ago 126MB liumiaocn:ldap liumiao$步骤2: 启动服务
使用如下命令启动服务
执行命令:docker run -it --name=ldap -p 10389:10389 -d dwimberger/ldap-ad-it
执行日志如下所示:
liumiaocn:ldap liumiao$ docker run -it --name=ldap -p 10389:10389 -d dwimberger/ldap-ad-it 010c87b4d5532315415b251e521c6b0ebf9c89fea47dbf2eb2232801a211f663 liumiaocn:ldap liumiao$ docker ps CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES 010c87b4d553 dwimberger/ldap-ad-it "java -jar ldap-serv…" 2 seconds ago Up 1 second 0.0.0.0:10389->10389/tcp ldap liumiaocn:ldap liumiao$步骤3: 日志确认
liumiaocn:ldap liumiao$ docker logs ldap [main] WARN org.apache.directory.server.core.DefaultDirectoryService - ApacheDS shutdown hook has NOT been registered with the runtime. This default setting for standalone operation has been overriden. [main] DEBUG org.jboss.test.ldap.InMemorySchemaPartition - Initializing schema partition schema [main] WARN org.apache.directory.server.core.DefaultDirectoryService - You didn't change the admin password of directory service instance 'ds'. Please update the admin password as soon as possible to prevent a possible security breach. Directory service started in 2622ms Importing users.ldif dn: cn=microsoft, ou=schema cn: microsoft objectclass: metaSchema objectclass: top dn: ou=attributetypes, cn=microsoft, ou=schema ou: attributetypes objectclass: organizationalUnit objectclass: top dn: m-oid=1.2.840.113556.1.4.221, ou=attributetypes, cn=microsoft, ou=schema m-syntax: 1.3.6.1.4.1.1466.115.121.1.15 m-name: sAMAccountName m-oid: 1.2.840.113556.1.4.221 objectclass: metaAttributeType objectclass: metaTop objectclass: top m-equality: caseIgnoreMatch m-singlevalue: TRUE dn: m-oid=1.2.840.113556.1.4.222, ou=attributetypes, cn=microsoft, ou=schema m-syntax: 1.3.6.1.4.1.1466.115.121.1.15 m-name: memberOf m-oid: 1.2.840.113556.1.4.222 objectclass: metaAttributeType objectclass: metaTop objectclass: top m-equality: caseIgnoreMatch m-singlevalue: FALSE dn: m-oid=1.2.840.113556.1.4.223, ou=attributetypes, cn=microsoft, ou=schema m-syntax: 1.3.6.1.4.1.1466.115.121.1.15 m-name: objectCategory m-oid: 1.2.840.113556.1.4.223 objectclass: metaAttributeType objectclass: metaTop objectclass: top m-equality: caseIgnoreMatch m-singlevalue: TRUE dn: ou=objectclasses, cn=microsoft, ou=schema ou: objectClasses objectclass: organizationalUnit objectclass: top dn: m-oid=1.2.840.113556.1.5.6, ou=objectclasses, cn=microsoft, ou=schema m-may: memberOf m-must: sAMAccountName m-must: objectCategory m-name: simulatedMicrosoftSecurityPrincipal m-supobjectclass: top m-typeobjectclass: AUXILIARY m-oid: 1.2.840.113556.1.5.6 objectclass: metaObjectClass objectclass: metaTop objectclass: top Creating new partition for DN=dc=wimpi,dc=net dn: dc=wimpi,dc=net objectclass: top objectclass: domain dc: wimpi dn: ou=users,dc=wimpi,dc=net ou: users objectclass: organizationalUnit objectclass: top dn: uid=test,ou=users,dc=wimpi,dc=net uid: test objectcategory: User cn: Test User sn: test memberof: admin objectclass: top objectclass: person objectclass: inetOrgPerson objectclass: simulatedMicrosoftSecurityPrincipal samaccountname: test userpassword: secret dn: ou=roles,dc=wimpi,dc=net ou: roles objectclass: top objectclass: organizationalUnit dn: cn=admin,ou=roles,dc=wimpi,dc=net member: uid=test,ou=users,dc=wimpi,dc=net cn: admin objectclass: top objectclass: groupOfNames You can connect to the server now URL: ldap://127.0.0.1:10389 User DN: uid=admin,ou=system Password: secret LDAP server started in 2943ms liumiaocn:ldap liumiao$
注意:最后的信息,是LDAP管理账号的dn信息和密码,后续的验证中会用到。
连接验证本文我们使用Apache Directory Studio进行连接和结果验证,关于Apache Directory Studio的简介可参看:
- https://blog.csdn.net/liumiaocn/article/details/83991147
选中向导,点击Next按钮
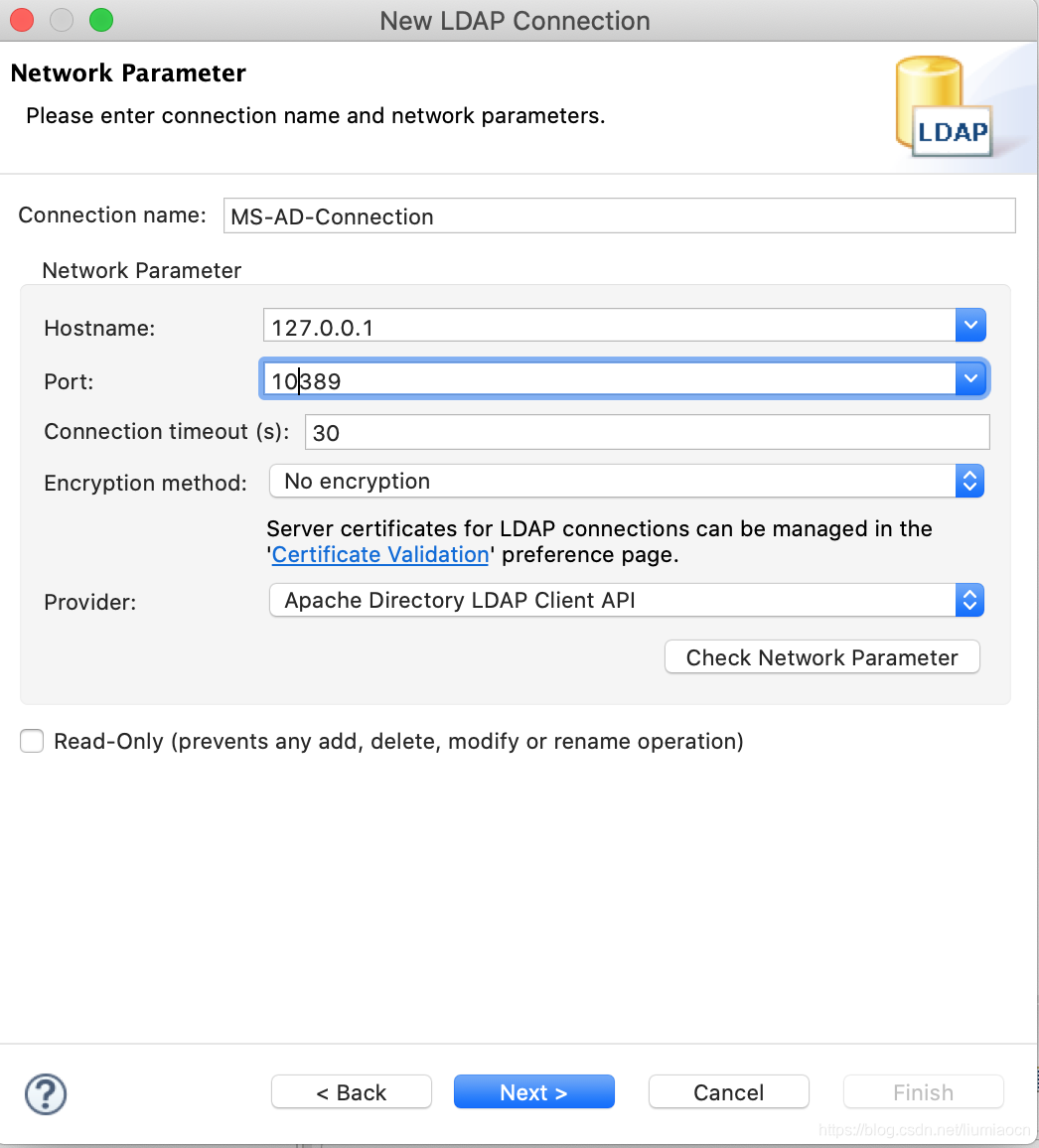
按照如下内容设定连接参数
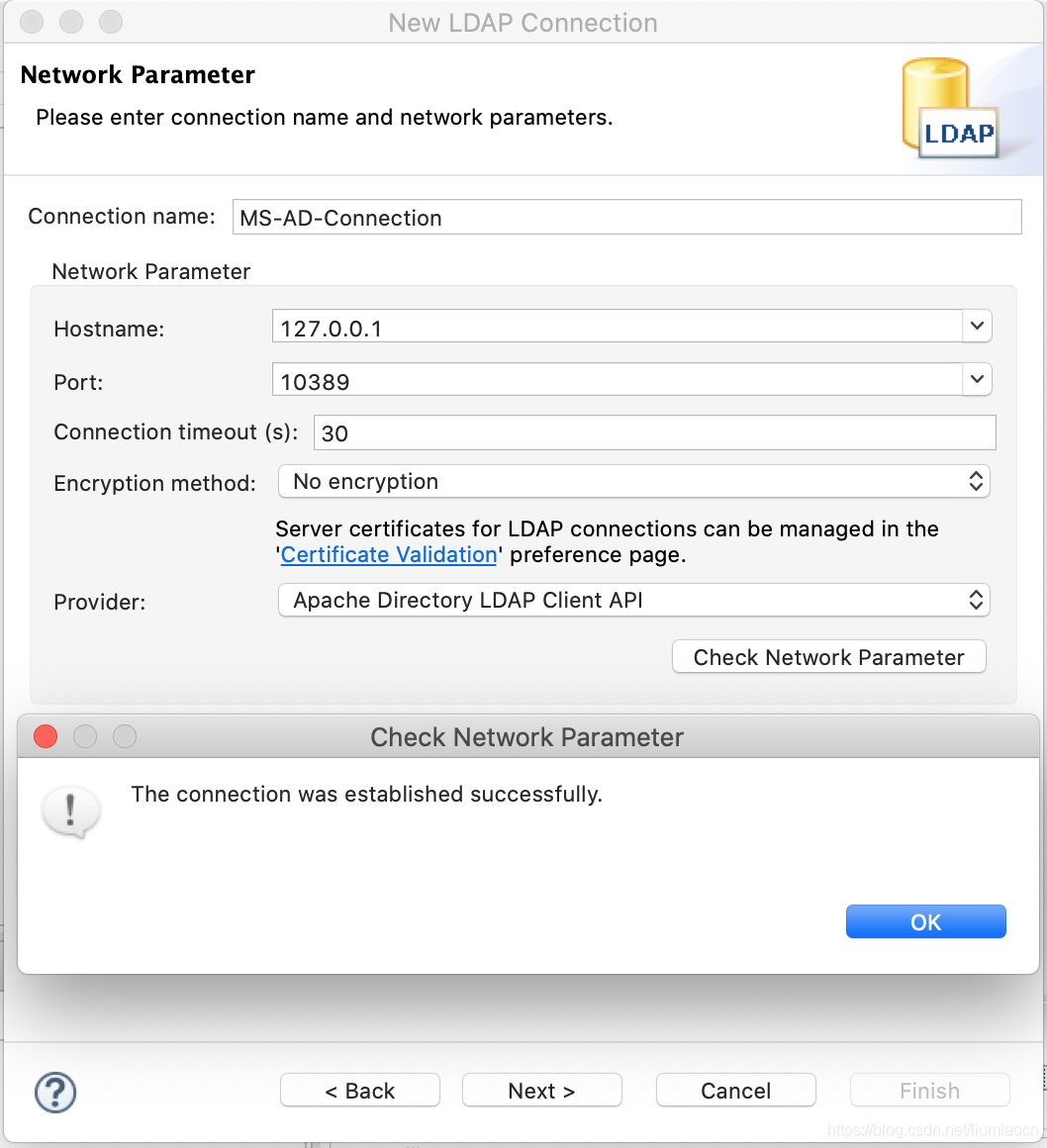
 点击Check Network Parameter按钮,如果出现如下成功提示信息,说明参数配置和服务启动都没有问题
点击Check Network Parameter按钮,如果出现如下成功提示信息,说明参数配置和服务启动都没有问题
 点击Next进行下一步的连接
点击Next进行下一步的连接
在如下页面,输入服务启动时日志中提示信息中的dn和password进行连接:
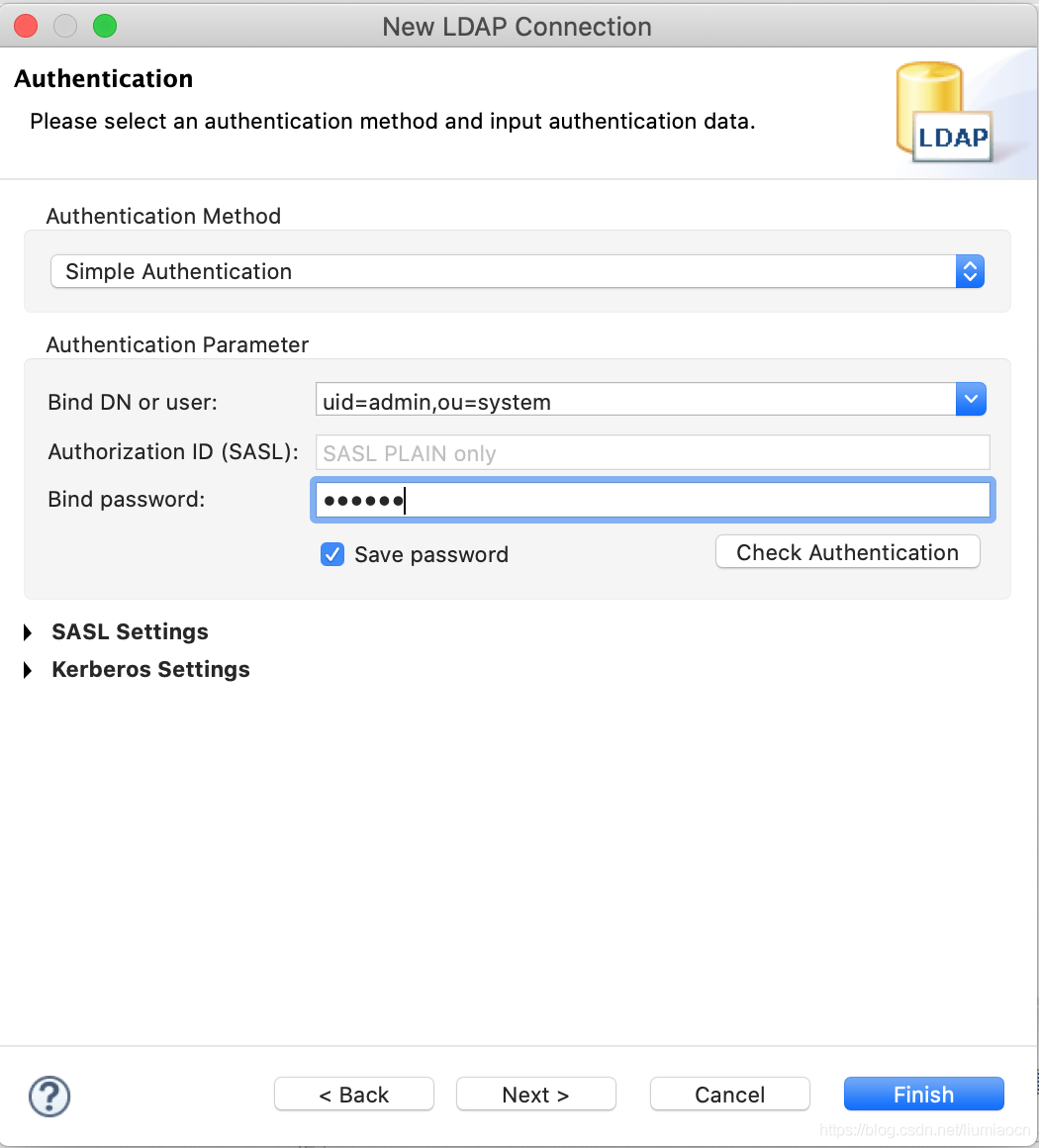 点击Check Authentication按钮进行检查,如果出现如下信息说明一切正常。
点击Check Authentication按钮进行检查,如果出现如下信息说明一切正常。
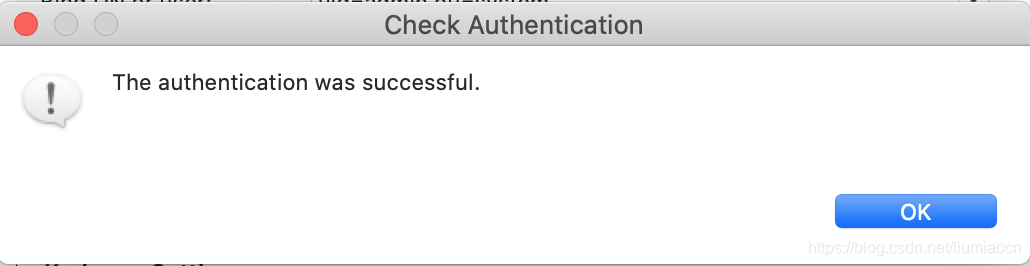
一切正常的情况下,连接成功后就可以通过Apache Directory Studio进行操作了,详细信息如下所示:
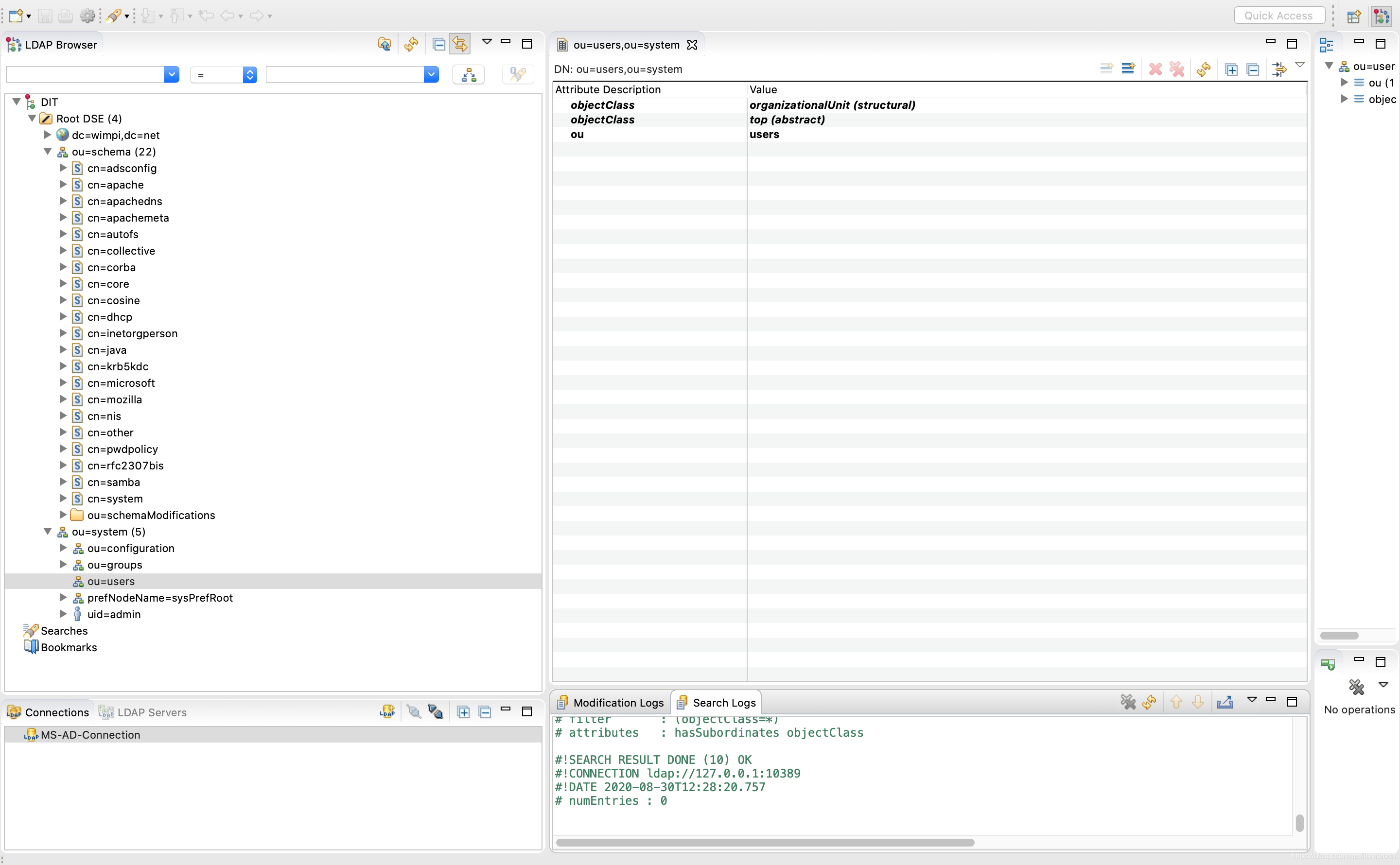
容器化改变了环境配置的方式,而生态注定将是关键的内容,连AD这种东西都有人放到容器中,虽然可能只是模拟,暂时虚拟化的方向已经是无可取代。



