网络中有VLAN用户若干,有三条出口。在核心交换机上设置策略路由,使核心交换机根据预先设置好的ACL流的匹配来决定将数据库丢往三个出口的其中一个。
简单配置步骤如下:
一、网络说明
设备管理地址: 核心交换机:型号Quidway S8508,IP 192.168.0.254(vlan1) 楼层交换机:型号Quidway 3600-28TP-SI,IP 192.168.0.20 – 192.168.0.28(vlan1)
内网VLAN及IP地址: 192.168.0.0/24,vlan1,服务器及用户A段IP 192.168.1.0/24,vlan2,用户B段IP 192.168.2.0/24,vlan3,用户C段IP 192.168.3.0/24,vlan4,用户D段IP 10.8.0.0/24,vlan5,用户E段IP
三个出口设备内网IP地址: 外网1出口防火墙内网IP地址:192.168.0.11,所在核心交换机端口:inter gig 3/3/1 外网2出口防火墙内网IP地址:192.168.0.12,所在核心交换机端口:inter gig 3/3/2 外网3出口防火墙内网IP地址:192.168.0.13,所在核心交换机端口:inter gig 3/3/3
分布: 楼宇A:所在核心交换机端口:inter gig 6/1/1,存在vlan:vlan1、vlan3、vlan5 楼宇B:所在核心交换机端口:inter gig 6/1/2,存在vlan:vlan1、vlan4、vlan5 楼宇C:所在核心交换机端口:inter gig 6/1/3,存在vlan:vlan1、vlan2、vlan4、vlan5 楼宇D:所在核心交换机端口:inter gig 6/1/4,存在vlan:vlan1、vlan2、vlan3、vlan5 网络中心服务器群:所在核心交换机端口:inter gig 3/1/1,存在vlan:vlan1
网络拓扑图:
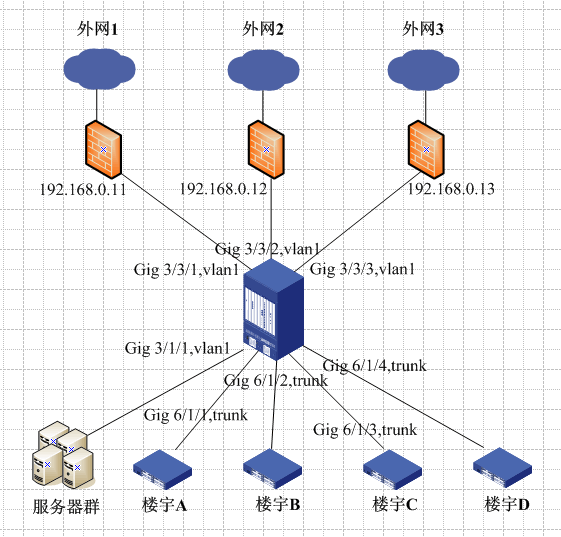
二、实现功能
1、当楼宇A、B、C、D中vlan1、vlan2及vlan3的用户电脑访问网络时从外网1也就是核心交换机的gig 3/3/1端口上出去 2、当这些楼宇中的vlan4的用户电脑访问网络时从外网2出口出去 3、当这些楼宇的vlan5中的用户电脑访问网络时从外网3出口出去 4、所有vlan均能访问vlan1的服务器群网段
三、配置步骤
思路:首先建立一个普通的三层网络,在核心交换机上利用默认路由将楼宇交换机来的数据包全部丢到核心的192.168.0.11上也就是外网1出口上,然后在接楼宇端口上利用核心交换机的traffic-redirect功能通过源地址acl流匹配将vlan4和vlan5的数据包丢到192.168.0.12(外网2)或192.168.0.13(外网3)上。
1、在核心上建立三层网络,并配置好各楼宇交换机,这里略过。然后在核心交换机上添加一条默认路由,这样所有的数据包就都从外网1出口出去:
ip route-static 0.0.0.0 0.0.0.0 192.168.0.11 preference 60
2、因为在接楼宇端口上应用traffic-redirect后数据包就直接丢到外网的内网口了,这样vlan4和vlan5访问vlan1的服务器群就有问题了。所以我们先在端口上做acl。
建立acl:
[center] acl number 3001 [center acl number 3001] rule 0 permit ip source 192.168.3.0 0.0.0.255 destination 192.168.0.0 0.0.0.255 [center acl number 3001] rule 1 permit ip source 10.0.8.0 0.0.0.255 destination 192.168.0.0 0.0.0.255
下发楼宇A端口:
[center] inter gig 6/1/1 [center-GigabitEthernet6/1/1] packet-filter inbound ip-group 3001
其他楼宇端口下发方法相同,这里略过。另外,对于是vlan1属性的inter gig 3/1/1,因为端口下只有一个vlan,所以就不需要做策略路由。在下发顺序上也是应该也下发acl规则,然后再下发策略路由。这样就可以先匹配内网的访问需求了。
3、在连接楼宇交换机的核心交换机端口上做策略路由
建立vlan4的acl流匹配规则:
[center] acl number 3002 [center-acl number 3002] rule 0 permit ip source 192.168.3.0 0.0.0.255
建立vlan5的acl流匹配规则:
[center] acl number 3003 [center-acl number 3003] rule 0 permit ip source 10.8.0.0 0.0.0.255
下发针对vlan4的楼宇A端口的下一跳路由:
[center] inter gig 6/1/1 [center-GigabitEthernet6/1/1] traffic-redirect inbound ip-group 3002 next-hop 192.168.0.12
下发针对vlan5的楼宇A端口的下一跳路由:
[center] inter gig 6/1/1 [center-GigabitEthernet6/1/1] traffic-redirect inbound ip-group 3003 next-hop 192.168.0.13
这样配置后,vlan1至vlan3仍然从核心交换机的默认路由192.168.0.11外网1出口出去。如果源地址为192.168.3.0网络地址进入核心交换机的连接楼宇的端口后,针对源地址为192.168.3.0的acl规则3002就被匹配,这样就被路由至192.168.0.12的外网2出口上。同理如果是源地址为10.8.0.0网络的地址流入核心交换机的端口上则根据端口定义好的下一跳路由它将被送往192.168.0.13的外网3网络上。
最后附上核心交换机的完整配置:
# sysname center # radius scheme system server-type huawei primary authentication 127.0.0.1 1645 primary accounting 127.0.0.1 1646 user-name-format without-domain
domain system radius-scheme system access-limit disable state active idle-cut disable self-service-url disable
domain default enable system # local-server nas-ip 127.0.0.1 key huawei # Xbar load-single # temperature-limit 3 10 65 temperature-limit 4 10 50 temperature-limit 5 10 50 temperature-limit 6 10 65 # dot1x # acl number 3001 rule 0 permit ip source 10.10.6.0 0.0.0.255 destination 192.168.0.0 0.0.0.255 rule 0 permit ip source 192.168.3.0 0.0.0.255 destination 192.168.0.0 0.0.0.255 acl number 3002 rule 0 permit ip source 192.168.3.0 0.0.0.255 acl number 3003 rule 0 permit ip source 10.8.0.0 0.0.0.255 # vlan 1 description bangong_and_server # vlan 2 description user_a # vlan 3 description user_b # vlan 4 description user_c # vlan 5 description user_d # interface Vlan-interface1 description bangong_and_server ip address 192.168.0.254 255.255.255.0 # interface Vlan-interface2 description user_a ip address 192.168.1.254 255.255.255.0 # interface Vlan-interface3 description user_b ip address 192.168.2.254 255.255.255.0 # interface Vlan-interface4 description user_c ip address 192.168.3.254 255.255.255.0 # interface Vlan-interface5 description user_d ip address 10.8.0.254 255.255.255.0 # interface Aux4/0/1 # interface M-Ethernet4/0/0 # interface GigabitEthernet3/1/1 description to_server-group # interface GigabitEthernet3/1/2 # interface GigabitEthernet3/1/3 # interface GigabitEthernet3/1/4 # interface GigabitEthernet3/2/1 # interface GigabitEthernet3/2/2 # interface GigabitEthernet3/2/3 # interface GigabitEthernet3/2/4 # interface GigabitEthernet3/3/1 description to_waiwang1 # interface GigabitEthernet3/3/2 description to_waiwang3 # interface GigabitEthernet3/3/3 description to_waiwang3 # interface GigabitEthernet3/3/4 # interface GigabitEthernet6/1/1 port link-type trunk port trunk permit vlan all packet-filter inbound ip-group 3001 rule 0 system-index 1 packet-filter inbound ip-group 3001 rule 1 system-index 2 traffic-redirect inbound ip-group 3002 rule 0 system-index 3 next-hop 192.168.0.12 traffic-redirect inbound ip-group 3003 rule 0 system-index 4 next-hop 192.168.0.13 # interface GigabitEthernet6/1/2 port link-type trunk port trunk permit vlan all packet-filter inbound ip-group 3001 rule 0 system-index 5 packet-filter inbound ip-group 3001 rule 1 system-index 6 traffic-redirect inbound ip-group 3002 rule 0 system-index 7 next-hop 192.168.0.12 traffic-redirect inbound ip-group 3003 rule 0 system-index 8 next-hop 192.168.0.13 # interface GigabitEthernet6/1/3 port link-type trunk port trunk permit vlan all packet-filter inbound ip-group 3001 rule 0 system-index 9 packet-filter inbound ip-group 3001 rule 1 system-index 10 traffic-redirect inbound ip-group 3002 rule 0 system-index 11 next-hop 192.168.0.12 traffic-redirect inbound ip-group 3003 rule 0 system-index 12 next-hop 192.168.0.13 # interface GigabitEthernet6/1/4 port link-type trunk port trunk permit vlan all packet-filter inbound ip-group 3001 rule 0 system-index 14 packet-filter inbound ip-group 3001 rule 1 system-index 15 traffic-redirect inbound ip-group 3002 rule 0 system-index 16 next-hop 192.168.0.12 traffic-redirect inbound ip-group 3003 rule 0 system-index 17 next-hop 192.168.0.13 # interface GigabitEthernet6/2/1 # interface GigabitEthernet6/2/2 # interface GigabitEthernet6/2/3 # interface GigabitEthernet6/2/4 # interface GigabitEthernet6/3/1 # interface GigabitEthernet6/3/2 # interface GigabitEthernet6/3/3 # interface GigabitEthernet6/3/4 # interface NULL0 # ip route-static 0.0.0.0 0.0.0.0 192.168.0.11 preference 60 # snmp-agent snmp-agent local-engineid 80507DBD05757576F5DD55A46877 snmp-agent community write jsisaa snmp-agent sys-info version all # user-interface con 0 user-interface aux 0 user-interface vty 0 4 user privilege level 3 set authentication password simple winsaaa # return



